Vulnerability Management
Vulnerability management is a key part of ORNA's "Prevent" feature set designed to help you prevent damaging cyberattacks from happening in the first place. ORNA's Scout monitoring agent automatically scans all assets it's installed and active on for vulnerabilities a threat actor can exploit, cross-references them with NVD's CVSS score, and displays them within the Vulnerabilities dashboard in real-time.
Each vulnerability's Severity score is displayed alongside the current Criticality rating of its' respective asset, allowing you to prioritize mitigation activities based on the correlation. For example, you should prioritize mitigating high-severity vulnerabilities discovered within high-criticality assets for the best impact.
NoteThe Vulnerabilities dashboard will be empty if you haven't installed ORNA's Scout agent on at least a single asset.
To access the Vulnerabilities dashboard, navigate to the Vulnerabilities tab.
Vulnerability Management features
- Key Performance Indicators are summarized at the top:
- Total Vulnerabilities
- Top 5 Vulnerabilities
- Top 5 Vulnerable Assets
- Top 5 Affected Systems
- The list of all vulnerabilities within your monitored assets known to Scout, cross-referenced with each asset's criticality, CVSS scoring, and containing links to relevant resources for further research.
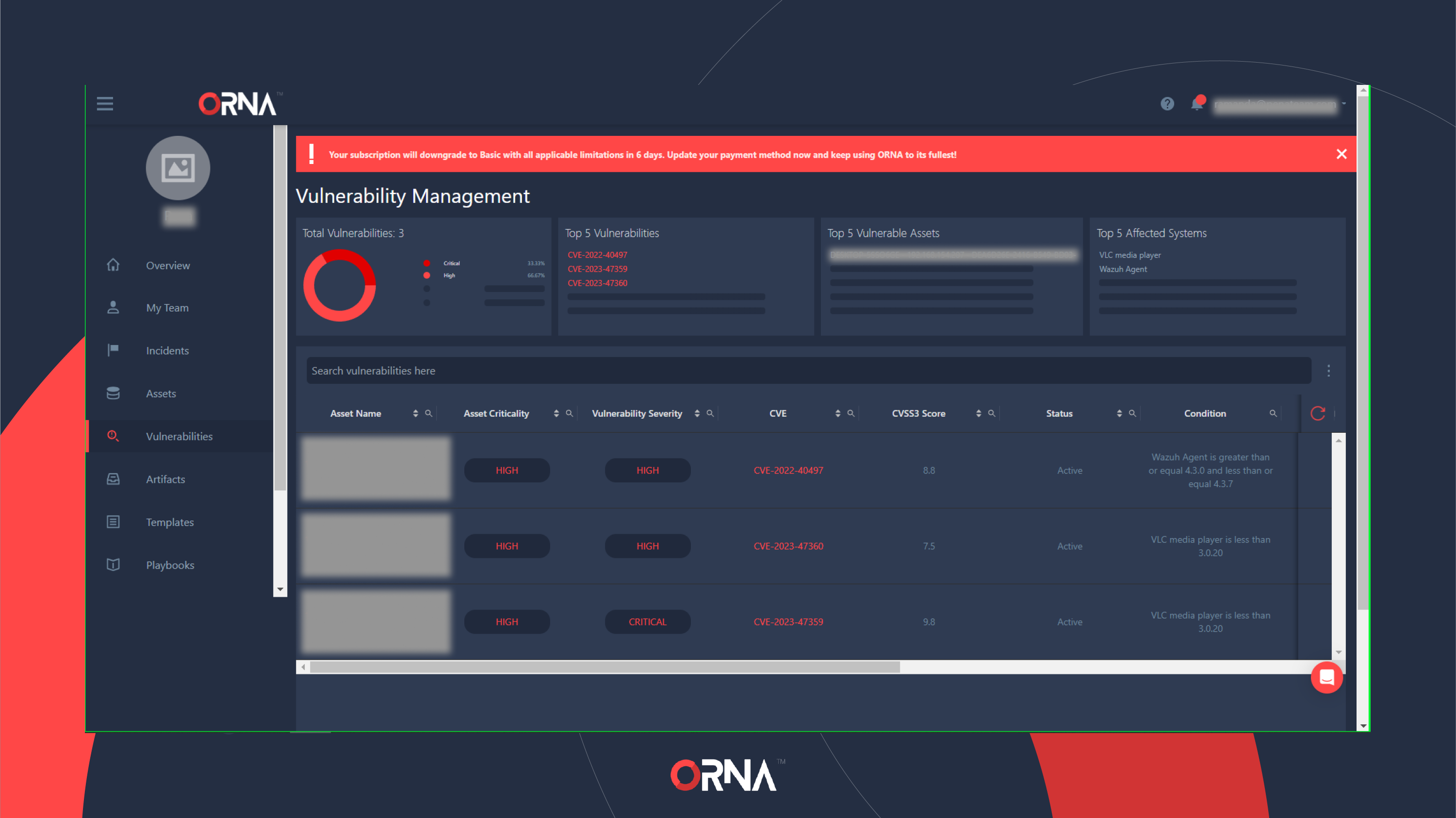
Vulnerability Management dashboard (partial)
Installing ORNA's Scout Agent
- Navigate to the Assets section on the sidebar of the platform.
- Click the View Agent Installation Instructions link located on the right-hand side of the assets table and follow the prompts.
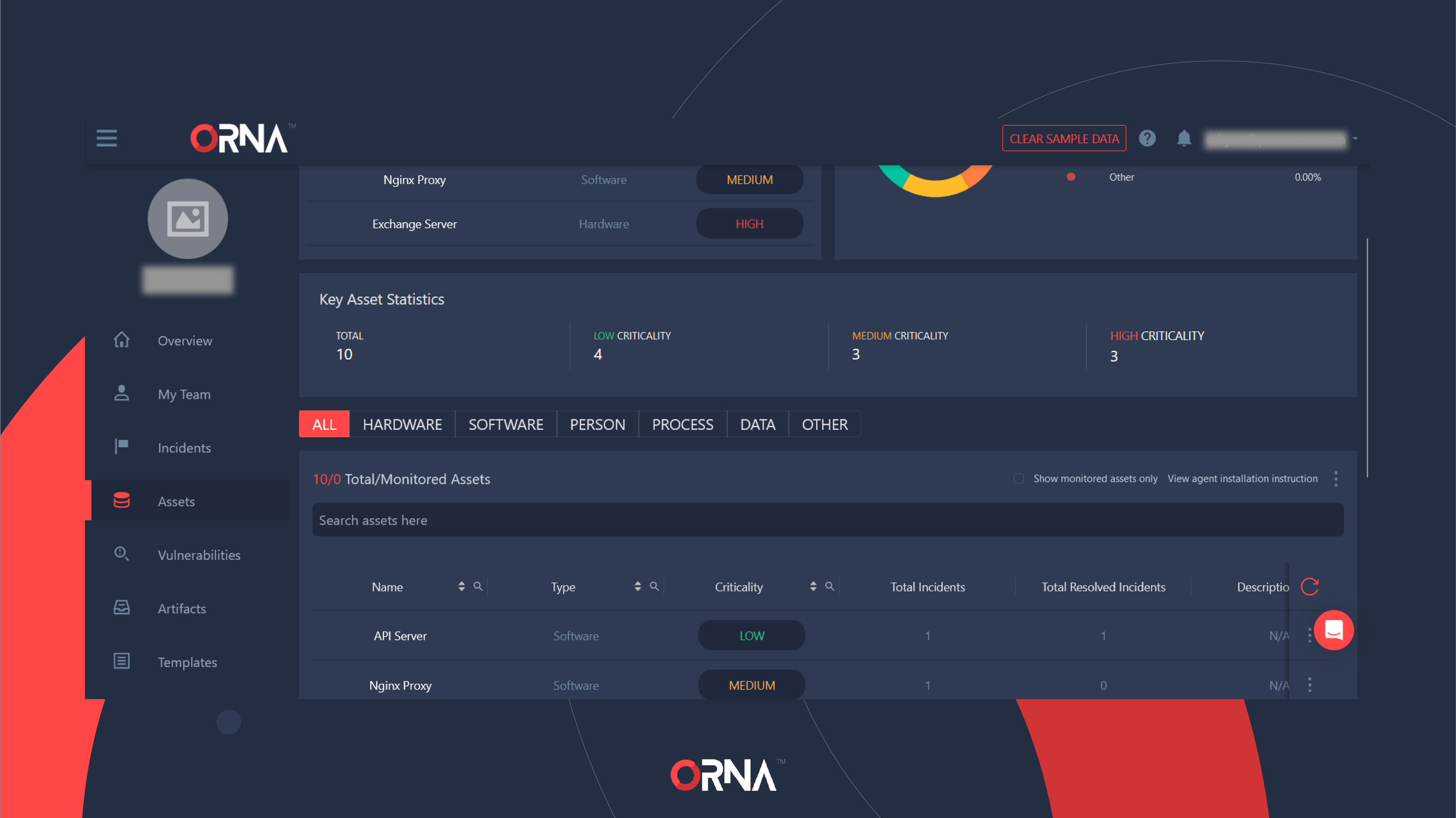
Assets dashboard (partial)
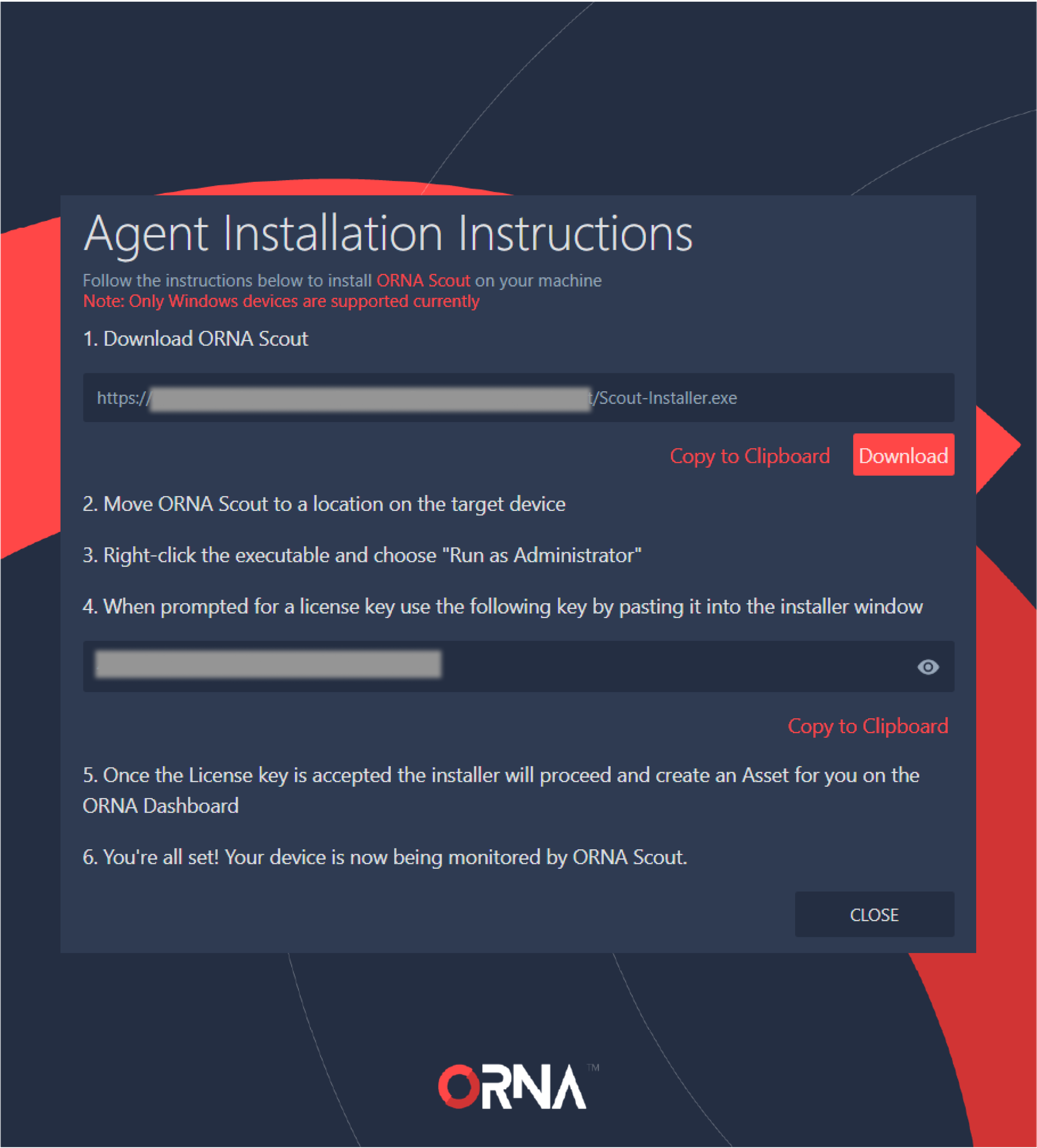
ORNA Scout installation instructions
- After Scout is installed, it runs continuously in the background, enabling ORNA's Alerts-related features, such as threat detection, cross-correlation, de-duplication, triage, and more, as well as automatically performs vulnerability scans, populating the Vulnerabilities dashboard and the relevant Key Performance Indicators.
Mitigating Vulnerabilities
- Navigate to the Vulnerabilities dashboard to view the list of vulnerabilities within the assets ORNA Scout currently monitors.
- Each active vulnerability contains links to NVD and CVE resources, where you can find detailed descriptions, mitigation steps, and more.
- Follow the relevant mitigation steps for each vulnerability.
- Once a vulnerability is mitigated (e.g., eliminated via a patch), it will still appear in the dashboard for reference purposes; however, its' status will be Solved instead of Active, and it will not count towards the Key Performance Indicators displayed at the top of the Vulnerability Management section.
Updated 9 months ago
