Respond
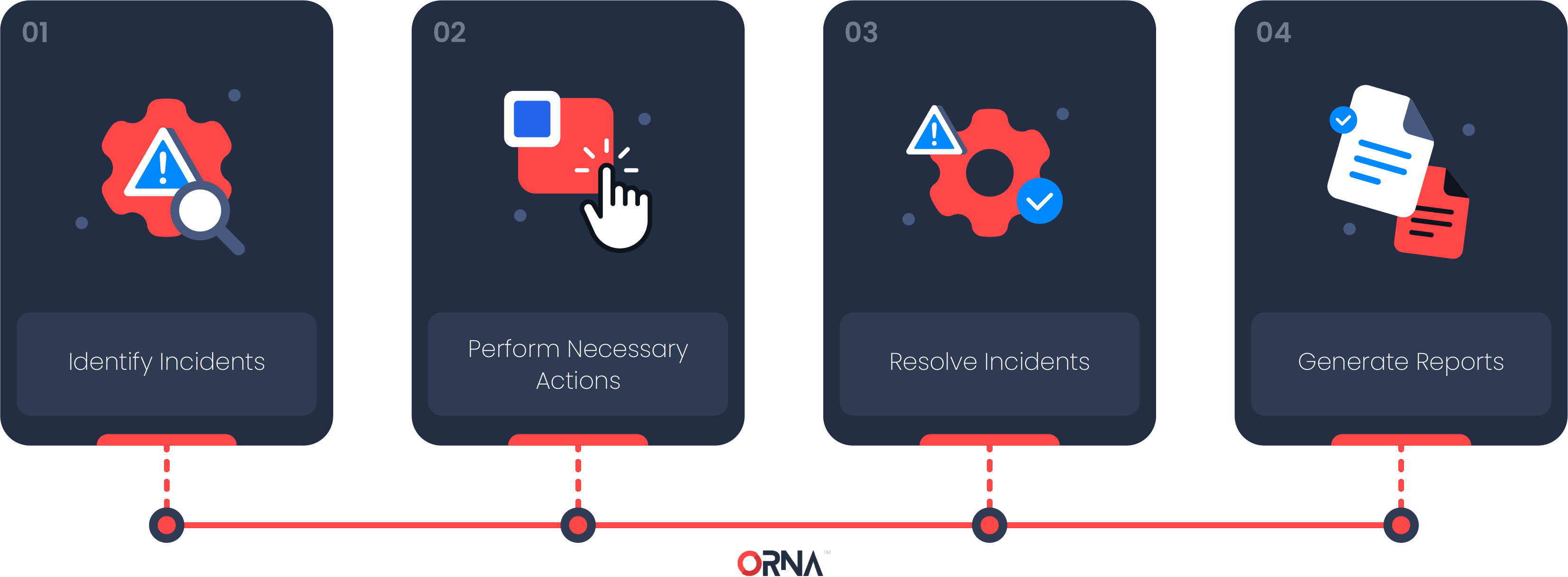
This guide provides an overview of ORNA’s “Respond” feature set, designed to streamline incident response procedures for significant security breaches, minimizing downtime and financial and reputation damage to your organization.
Step 1: Identify incidents and invoke Playbooks
First, create a new Incident by upgrading an Alert or manually creating one. Once a new Incident is created, ORNA will automatically:
NoteBrowse this guide's Alert Management or Incident Management sections to learn more about either incident creation option.
- Invoke a highly detailed Playbook (such as Ransomware or Insider Threat) to guide your organization through the most efficient incident response process.
- Automatically escalate and assign highly detailed, step-by-step incident response Tasks to each of your team members, eliminating guesswork.
- Create a collaborative Trello-like incident management dashboard for each SANS incident response stage: Identification, Containment, Eradication, Recovery, and Lessons Learned.
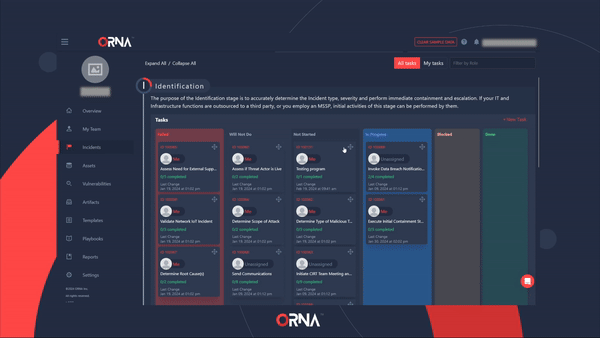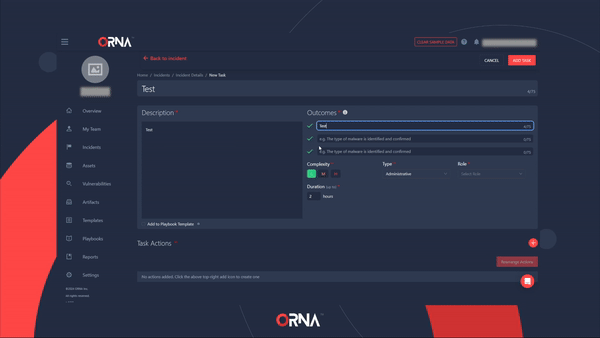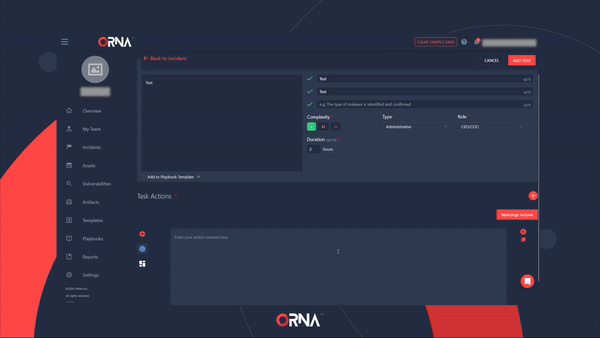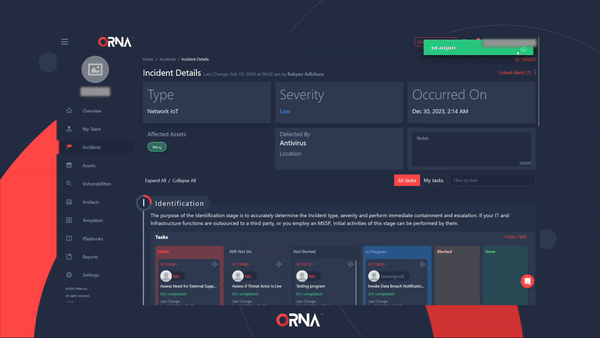
Creating a custom Task in an active Incident
- Collect and track all progress and evidence (known as Artifacts).
- Provide internal and external Communications templates, including regulatory compliance management and progress updates.
- Allow for secure team communications using the built-in secure out-of-bounds Chat function.
Step 2: Perform incident response tasks and manage your team
- Navigate to the Incident Details screen by clicking on an Incident record either in the Overview dashboard or the Incidents section.
- View the incident resolution progress at a glance using the Task management board divided into SANS incident response stages: Identification, Containment, Eradication, Recovery, and Lessons Learned.
- See and track the status of the Tasks of each of your team members, including Done, Not Started, Blocked, Failed, and more.
- Create new custom Tasks, reassign Tasks as needed, and inquire about the progress using the built-in secure Chat function.
- Click on any Task to view its details, such as Description, Outcomes, and specific, step-by-step resolution Actions.
- Perform the relevant Actions and check the checkbox once you finished them.
- Upload Artifacts (evidence) relevant to the Task using the “Add New” function.
- Easily change the status of any Task by dragging it to the desired stage or automatically mark it as Done once all Actions have been completed.
- Stuck? Get live 24/7 incident response assistance from our expert SecOps team using the support chat in the bottom right corner of the screen.
Step 3: Resolve incidents
- Navigate to the Incident Details screen by clicking on an Incident record either in the Overview dashboard or the Incidents section.
- Click the “...” Options button in the top right corner of the Incident Details screen and select “Resolve” from the list.
- Type “resolve incident” in the confirmation popup, select the desired disposition label (“Ignore” for a false positive, “Resolved” for an actual incident), and click Confirm.
- This Incident will now be marked as Resolved, and you can generate a highly detailed report for it in the Reports section.
Step 4: Generate reports based on resolved incidents
- Navigate to the Reports section on the sidebar of the platform.
- Click the “...” Options button on the right-hand side of the incident record for which you'd like to generate a new report.
- Select the Generate Report option. A popup will appear, allowing you to customize the level of detail that this PDF report should include.
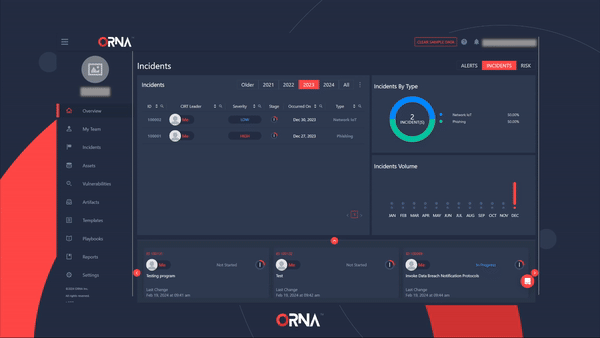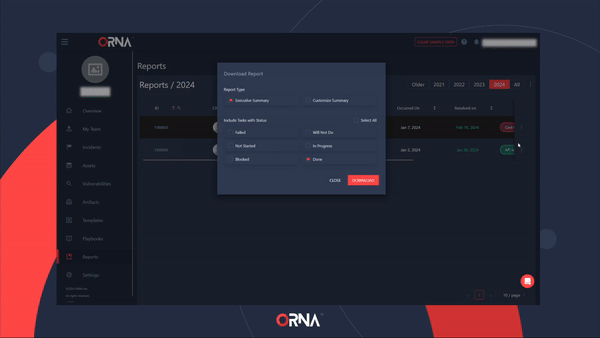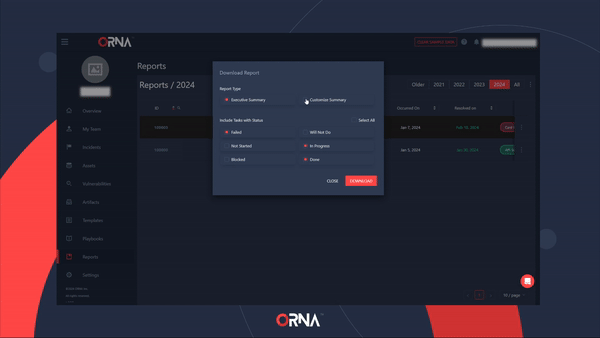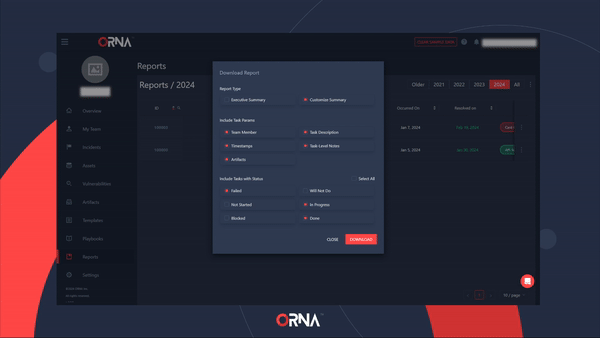
Generating a PDF report for a resolved Incident
- After selecting the desired report options, click Download. Your PDF report will be downloaded shortly.
- To access the report, you must input its unique auto-generated password. To obtain the password, click the “...” Options button on the right-hand side of the incident record to which the report belongs. Select View Password and copy the value.
- Due to the inherently sensitive nature of incident reports, please carefully consider the individuals you choose to share the report with its unique password, and the means of doing so.
Updated 10 months ago
